11 IoT security challenges and how to overcome them
IoT, while influential and beneficial, introduces several security challenges, from device discovery and patching to access control and cyber attacks.
The internet of things is all around us -- from the smart watch on your wrist measuring your heart rate, to the smart speaker playing music to smart traffic management systems that optimize streetlight patterns and alleviate congestion on roadways, to sensors on trash receptacles that report when they're nearly full to improve sanitation and the efficiency of garbage collection.
In buildings, smart devices and systems help conserve energy by adjusting the thermostat and turning off the lights in empty rooms. In healthcare, they monitor patients and equipment. In manufacturing plants and industrial IoT use cases, they track assets and monitor wear and tear on machines to predict when they will need repairs.
Despite these beneficial use cases, however, IoT increases the security risks businesses and consumers face. Any device that connects to the internet could be an entry point to the larger network -- and the sensitive information it contains. Such cyber attacks can be detrimental to a business or, in some cases, life-threatening or deadly.
IoT has expanded the attack surface tremendously. Before diving into an IoT implementation, it is important to prepare for the numerous issues IoT presents. Here are 11 of the many inherent IoT security challenges and how to mitigate them.
This article is part of
Ultimate IoT implementation guide for businesses
1. Device discovery and management
You can't protect what you can't see.
It's one of the oldest security adages around. Before thinking about network and device security, it's important to know what exactly needs to be secured.
Port scanning, protocol analysis and other detection techniques can determine which devices are connecting to corporate networks. Free tools such as Nmap, Shodan and Masscan are available, as well as commercial products and services that discover, identify and manage IoT devices.
Once IoT devices are discovered, perform an IoT risk assessment to understand what the devices can -- and should -- have access to and why. List approved devices on an enterprise asset register, along with each device's associated patch management processes and lifecycle information. Include connected devices in penetration tests, too. Establish policies and capabilities to manage lost or stolen devices, such as remote wiping and disabling connectivity.
Vulnerable connected devices are not always obvious threats and often fall into the category of shadow IT. Be sure to consider connected printers, smart refrigerators and sensors added to machinery. Remember the Target point-of-sale data breach? It was caused by someone misusing a contractor's login to the company's connected HVAC system. Be aware of any shadow IoT devices through device discovery.
2. Authentication, authorization and access control
IoT devices have a unique identifier that can help with authentication and authorization. After discovering which devices connect to the network, decide what they can access and talk to. With hundreds or even thousands of unique IDs to deal with, however, this task can seem daunting.
Operate on the principle of least privilege to allow devices to see and access only what is necessary for them to do their job. Update any device that comes with a factory-installed password. Strong passwords help combat IoT risks. Two-factor or multifactor authentication should be used wherever possible.
Generally speaking, hardware-based roots of trust are considered the strongest IoT security option. These are built directly into hardware and embedded onto a device. Digital certificates issued from a trusted public key infrastructure (PKI) can also be used, although some devices don't have the ability to process them. Other lightweight cryptographic algorithms may be used in this instance (more on that below).
Newer technologies, such as biometrics and blockchain, can also be used to authenticate IoT devices. Taking a zero-trust approach is also an effective option to control devices and access rights. Commercial IoT platforms also offer features to manage devices and control what data other devices and networks devices can access.
3. IoT passwords
Problematic passwords are related to authentication, authorization and access control. The 2016 Mirai infiltration attack was traced to connected cameras and other IoT devices that had factory-default or hardcoded passwords. The cybercriminals infiltrated servers using these devices and a list of known credentials -- a list that, by some accounts, only had 60 username/password combinations.
Responsibility here is twofold. Enterprises and end users should be diligent in updating default passwords, having a password policy and using strong passwords or passphrases. But this isn't an option if passwords are hardcoded. This is where device manufacturers must take their share of the blame. No device should be created with a hardcoded password, ever.
4. Patching and updates
Updating and patching devices is a critical component of any security strategy. One of the biggest IoT security challenges is the use of outdated software and firmware, including the OS, applications and communications technology.
IoT environments present several unique patching and updating challenges. First, some devices are inaccessible. What if sensors are dispersed across hundreds of acres of farmland to detect temperature, humidity and moisture? Or what if they're on top of a bridge monitoring its vibration and the weather?
Second, not all devices can be taken offline for long periods of time to perform updates. Think about critical manufacturing equipment that could cost an industrial organization millions of dollars if it's offline for an hour, or a smart grid that millions of people depend on for heat or electricity.
Third, add in the fact that some IoT devices have no UI or screen, and some won't even accept updates. Or what if a device does accept updates but something in an update corrupts it and causes system failure? How will the device be rolled back to a known-good state?
Vendors can create patching woes, too. Some devices may reach end of life and no longer be supported by the manufacturer. Similarly, some vendors don't release security updates when a vulnerability is discovered, leaving their customers open to security breaches.
To ensure IoT patching capabilities, enter each IoT device into an asset register as part of the device discovery or adoption process. Include which versions of software and hardware each device runs, and keep track of when updates are available and installed. Also, track when devices reach end of life and must be retired. Using legacy devices in live environments creates vulnerabilities.
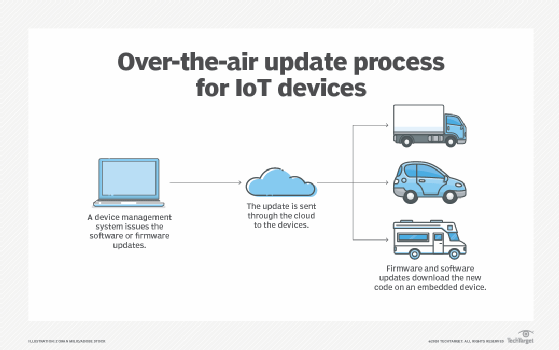
If possible, consider patching and updating processes before IoT deployments. Be sure over-the-air updates are available and secure. Also, decide between automatic updates and a periodic schedule, as each has its own set of benefits and drawbacks.
Choose an IoT platform wisely. Many contain features to ease patching and updating processes, such as automation, and can manage devices that need rollbacks or resets. Keep an eye on the Internet Engineering Task Force Software Updates for Internet of Things working group, which is developing a standard for IoT firmware updates.
5. IoT attacks
IoT environments are subject to many of the same threats as other cyber environments, including DDoS attacks, botnets, malware and ransomware.
To fully understand the severity of an IoT DDoS attack, look no further than the 2016 Mirai attacks. While the attacks initially targeted a Minecraft server host, the malware ended up first hitting security journalist Brian Krebs's website and French web host OVH. A month later, the botnet was used to target DNS service provider Dyn, resulting in downtime for several high-profile sites, including Amazon, Netflix and Twitter.
It is nearly impossible to prevent a DDoS attack. Organizations can take steps to prevent one from succeeding, however. Use intrusion prevention/detection systems (IPSes/IDSes) with DDoS features, or partner with an ISP that can detect and filter DDoS packets before they reach the network. Follow other basic cyber hygiene practices, including the use of firewalls, antimalware, endpoint security platforms, endpoint detection and response (EDR) and extended detection and response software.
To prevent botnet, ransomware and other IoT attacks, keep device software up to date, change default passwords and monitor network traffic. Segment which data and networks IoT devices can access, and use firewalls to stop intrusions. Disable any unnecessary features on devices, and regularly back up data from devices and networks. An IoT risk assessment can also help determine potential threats and their impact.

6. Physical security
IoT devices must be protected not only from cybersecurity threats, but also from physical security threats. Because IoT hardware -- including IoT sensors, wearables and edge devices -- is more easily accessible than other pieces of a network, it is subject to physical threats beyond hardcoded passwords, such as physical damage, tampering and theft.
Unsecured devices, if physically broken into, could have their ports connected to a device that exfiltrates data. Storage mechanisms could also be removed and data, stolen. This physical access also can be an entry point to the larger network.
To prevent physical security risks, IoT devices must be hardened. Embed security on the device, ensure proper access control, reset default passwords, encrypt data and connections, and remove or disable unused ports. Also, ensure IoT devices cannot be easily disassembled or have any of their components removed. In some scenarios, it is necessary to put devices in a tamper-resistant case or render the device unusable after physical tampering.
7. Encryption and data security
Encryption is considered the most effective way to secure data. Cryptography is a key mechanism to prevent privacy risks and protect the integrity of IoT data at rest and in transit among the user, company, customer, and other people or devices. It also helps ensure IoT privacy and builds trust between companies and users -- especially when personally identifiable information and sensitive data come into play, such as with embedded and connected medical devices. Encryption also prevents attackers from manipulating or falsifying data.
The problem is that many connected devices -- think small sensors collecting temperature, humidity or moisture data -- cause the greatest IoT security concerns because they don't have the power, processing or memory resources required to run traditional encryption algorithms, such as Advanced Encryption Standard (AES). Such devices must use an algorithm with high security but low computation -- one that considers the size, power consumption and processing capabilities of resource-constrained devices.
This is where lightweight cryptographic ciphers come in. Elliptical curve cryptography, for example, provides the security equivalent of Rivest-Shamir-Adleman, or RSA, but with smaller key sizes and operations that require less processing, making it an ideal option for devices with lower storage space, processing power and battery life. Other lightweight ciphers include Clefia, a lightweight AES; Enocoro, a hardware-oriented stream cipher; and Speck, an add-rotate-XOR cipher.
Experts also recommend using trusted security protocols, such as Transport Layer Security or Datagram TLS.
PKI is another tried-and-true security option. It can be embedded onto devices at the manufacturing or enterprise level. PKI, which issues unique identities and digital certificates to devices, supports the distribution and identification of public encryption keys, enabling users and devices to securely exchange data.
In addition to cryptography, define proper encryption key lifecycle management processes.
8. Network security
Securing IoT devices and the data they collect is important, and it is equally important to ensure the networks those devices connect to remain safe from unauthorized access and attacks. Use IPSes/IDSes, antimalware, firewalls, and network detection and response or EDR.
Another IoT security best practice is to segment the IoT environment from the rest of the network. Connecting operational technology (OT) networks to IT networks wasn't considered a threat in the past. OT networks didn't connect to the internet and, while sometimes subjected to hacks, did not pose an imminent threat to IT networks. Legacy OT systems -- some decades old -- often run their own proprietary systems, meaning modern security mechanisms could overlook their issues during routine checks. Because OT devices and machines cannot be easily or cost-effectively replaced, organizations must update, patch and secure them. With many so old they can't be patched anymore, this can become a time-consuming task for security teams.
Through network segmentation, organizations can put different networks or parts of networks into different zones to create subnetworks -- using one zone each for sales, finance, operations and so forth. Each zone should have its own customized security policies based on its users, devices and data.
A common gripe with network segmentation is that it impedes efficiency and connectivity. Using an IoT gateway can mitigate these issues. Acting as an intermediary between the device and the network, a security gateway has more processing power, memory and compute capabilities than the IoT devices connecting to it. It can, therefore, implement stronger security measures, such as firewalls and antimalware, closer to the devices, preventing security threats from passing through to the network.
In addition to antimalware, firewalls, IPSes/IDSes and network segmentation, combat IoT risks by ensuring port security, disabling port forwarding and never opening ports when not needed. Also, block unauthorized IP addresses.
Bandwidth is another common IoT challenge. As IoT networks scale and more connected devices connect to a network, business continuity (BC) challenges arise. If critical applications don't receive their required bandwidth, productivity and efficiency suffer. To ensure high availability of applications and services, consider adding bandwidth and boosting traffic management and monitoring. This not only mitigates BC challenges but also prevents potential losses. From a project planning standpoint, conduct capacity planning and watch the growth rate of the network so that future bandwidth demand can be met.
Another consideration with network security is which IoT communications protocols to use. Not all protocols are created equal, especially when it comes to security features. From Bluetooth and Bluetooth Low Energy to cellular, MQTT, Wi-Fi, Zigbee and Z-Wave, consider the IoT environment and its security needs before using a protocol. Insecure communications are prone to eavesdropping and man-in-the-middle attacks.
9. Lack of standardization
A standard is a set of specifications, rules or processes generally agreed upon by an industry and academia. Global standards help ensure consistency and compatibility among products and applications -- a necessity for IoT environments to function smoothly.
The IoT industry has been plagued by a lack of standardization from the start, both in terms of security and otherwise. Things are changing, however. Government and standards bodies have begun passing legislation and setting regulations to ensure security is built into devices.
Approved in 2018, California's SB-327, "Information privacy: connected devices," requires manufacturers to equip devices with "reasonable" security features, including a preprogrammed unique password for each device and a setting that requires a new password be created upon first use. Also, in 2018, the U.K. published "Code of Practice for Consumer IoT Security," which was followed by the European Telecommunications Standards Institute's Technical Specification 103 645, a standard to regulate the safety of consumer devices, in 2019. The U.S.'s 2020 IoT Cybersecurity Improvement Act required NIST and the U.S. Office of Management and Budget to develop guidelines and standards around security measures on IoT devices used by the federal government. In May 2021, a presidential executive order, "Improving the Nation's Cybersecurity," called for a consumer IoT labeling program to launch in 2023. The aim of the program is to inform consumers about the risks of their smart home devices.
Companies should keep abreast of any new standards -- government, consumer or otherwise. These will influence IoT device manufacturing and security standards in the future.
10. IoT skills gap
The skills gap has affected every industry, and IoT is no different. One thing that sets IoT apart from other industries is that it is still a new discipline. It is also a convergence of IT and OT, meaning those fluent in OT are likely not well versed in IT, and vice versa. In addition, IoT isn't a single discipline. Many skills are required to be a successful IoT professional, from cybersecurity and UX design to machine learning and AI knowledge to application development.
IoT-specific certifications and trainings have emerged, including some that are IoT security-specific, which provide a baseline knowledge of connected environments.
Closing the skills gap is challenging in any industry. Investing in trainings and certifications for in-house employees is one option. Hiring third parties and consultants for IoT-specific projects is another option, although it could get costly depending on the number of projects that need to be worked on. Projects can also be outsourced completely.
11. Remote work and smart home risks
The rise of remote work due to the COVID-19 pandemic and the continued abundance of remote workers present major security challenges to organizations, especially if employees' IoT devices -- from smart TVs, to connected baby monitors, to smart fridges -- use the same networks employees use to connect to their company's systems. An attacker who infiltrates a smart thermostat, for example, could also access confidential corporate data. Likewise, smart speakers could create a privacy disaster if they overhear conference calls or video chats.
Conduct security awareness training to warn employees about the dangers of smart home devices and put policies in place to prevent them from becoming an issue.







