Edge computing security risks and how to overcome them
IT administrators must incorporate the right strategies and tools to anticipate, prevent and overcome common edge computing security risks and realize the value of edge technology.
At this point, everyone knows that computing and networking pose security risks, and, clearly, new risks come with new types of computing. That's true of edge computing and, because it represents a fairly dramatic shift in the IT paradigm for most businesses, edge security risks can be particularly serious, and mitigating them is especially important.
Edge computing security considerations
Edge computing is the deployment of computing resources outside the data center, close to the point of activity that the computing supports, where a series of connected devices such as IoT elements link the edge device to users or applications. That shift in deployment practices removes edge computing resources from the protective physical, access and network security umbrella the data center provides.
Edge applications also represent a fairly dramatic shift in the IT paradigm for most businesses, to a machine-to-machine (M2M) model lacking human oversight. Thus, edge security risks can be particularly serious. Understanding them and their remedies is critical to ensuring smooth business operations.
What is edge computing security?
Edge computing security is the process of providing whatever additional security is required to bring edge security up to data center standards for security and compliance. That means securing access to edge devices, both physically and through a user interface, in a way that is as effective as prevailing data center technologies, but suitable for deployment outside the data center.
Edge security is impossible without at least some control over physical access to edge elements, including both the edge computing device and any local access interfaces, terminals or portals. The goal in edge computing security is to recognize that the best edge physical security will fall short of what's available in the data center, and to deal with that reality first. The second step is to bring network, application and data security practices at the edge as close to data center standards as possible.
How can edge computing benefit security?
Edge computing doesn't always add risk. Most edge applications are variants on M2M or IoT, which means they rely on simple devices with limited built-in security features. By terminating the connection to these devices locally and applying more traditional encryption and access security protection on the connection between the edge and the cloud or data center, edge computing reduces the vulnerable attack surface of applications.
Even where the edge supports laptops, desktops or mobile devices that are powerful enough to have strong security features, getting their traffic onto a single connection to a company VPN or data center will improve monitoring and control of security. The edge computing facility can also help isolate local devices from denial-of-service attacks providing a security layer between these devices and the VPN or internet.
Common edge computing security risks
Edge computing is, in most ways, a kind of minimized data center, and minimization can often mean that protection features are stripped out or reduced to lower the cost of the edge facility. This is the biggest single source of incremental security risk in edge computing, but it's not the only source. To understand more, we'll need to look at specific risk factors and their sources.
1. Data storage, backup and protection risks
Data stored at the edge, as already noted, lacks the physical security protections usually found in data centers. In fact, it might be possible to steal an entire database simply by removing the disk from the edge computing resource, or by inserting a memory stick to copy information. Because edge computing facilities often have limited local storage options, it might also be difficult or even impossible to back up critical files, which means if an incident occurs, there might not be a backup copy to restore the database.
2. Password and authentication risks
Edge computing resources are rarely supported by local IT operations professionals who are security conscious. In many cases, maintaining the edge systems might be a part-time job assigned to several people, and this situation encourages lax password discipline, including accepting default passwords, using simple passwords easily remembered, posting notes with passwords for critical applications and failure to change passwords often. Edge systems might not employ strong authentication measures such as multifactor or two-stage authentication, again, for the convenience of users and administrators.
3. Perimeter defense risks
Because edge computing expands the IT perimeter, it complicates perimeter defense overall. Edge systems themselves might have to authenticate their applications with partner applications in the data center, and the credentials for this are often stored at the edge. That means a breach of edge security might expose access credentials to data center assets, increasing the scope of the security breach considerably. Because security tools might be limited at the edge by architecture differences in hosting, dealing with perimeter threats can be more difficult.
Cloud adoption risks
Cloud computing remains the hottest topic in IT, overall, so the risks associated with edge computing in combination with cloud computing are particularly important. What those risks are depends on the specific relationship between edge and cloud -- something that's easy to lose track of, because different cloud software platforms and services treat edge elements in different ways. If the edge devices are simple controllers, as is often the case, it can be difficult to give them secure access to cloud resources and applications. That makes the evaluation of cloud-to-edge connection, access control and general security measures especially important.
All the major public cloud providers offer tools to extend cloud features onto the premises, making the edge functionally a part of the cloud. This means that cloud security tools might be available to help with edge security, but it also means that it's harder to apply familiar security tools and practices within the cloud providers' edge frameworks.
Edge and IoT security risks
Edge applications relating to IoT pose special security risks because IoT devices are designed for low cost, low power usage and deployment to areas often not suitable for complex technology because of conditions in the environment where they're deployed, such as temperature and humidity, dust or vibration. These risks include the following:
- use of specialized M2M protocols, which normally lack sophisticated security features such as encryption;
- wireless interfaces such as Wi-Fi, which could be subject to hacking or hijacking because of easy access to the area where the Wi-Fi hubs are installed; and
- dependence on specialized IoT or industrial controllers as edge computing resources, when these specialized devices are difficult for users to upgrade with proper security software.
Edge security best practices
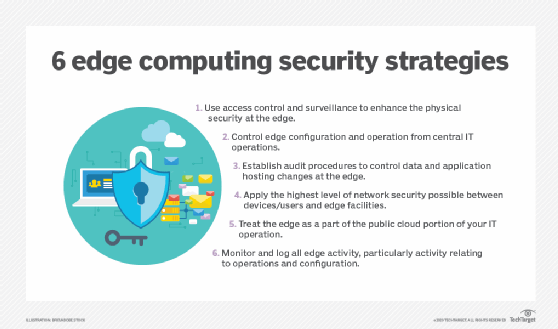
The following are six basic rules for edge computing security:
- Use access control and surveillance to enhance physical security at the edge.
- Control edge configuration and operation from central IT operations.
- Establish audit procedures to control data and application hosting changes at the edge.
- Apply the highest level of network security possible between devices/users and edge facilities.
- Treat the edge as a part of the public cloud portion of your IT operation, something independent and different that must be treated and secured through its own set of tools and practices.
- Monitor and log all edge activity, particularly activity relating to operations and configuration.
Access to edge facilities must be secured because the facility overall is not. Having the systems in a cage, ensuring that access to the cage is controlled and that video can identify access attempts is a good strategy. Opening the secure cage should trigger an alarm in the company's IT operations or security center. The tools for this are the same as those used for facility security: sensors and alarms.
Speaking of company IT operations, the organization, rather than local personnel, should oversee all edge configuration and operations. Having local people perform critical systems functions lends itself to careless password control and operating errors.
Edge application and data hosting should also be centrally controlled and subject to compliance audit. This can reduce or prevent incidents where critical application components or data elements are migrated to edge facilities that haven't been certified as secure to host them.
Because the network connection to the edge is the conduit for all edge information and all operations practices and messages, it's critical that the network connection be fully secure. That means high-quality encryption, using a technique that avoids storing keys on the edge system, because that system is less secure. Multifactor authentication or a carefully controlled physical security dongle should be required for all network, application and operation access, and edge computing resources that use Wi-Fi should be on their own separate Wi-Fi network, with measures to ensure that others can't gain the password and log on.
All of this must be monitored, and every event associated with edge computing operations, including all deployments, configuration changes and accesses to any supervisory modes from either a local keyboard/screen or remotely, must be logged and audited. Ideally, operations personnel in both the IT operations and security areas should be advised before making changes, and an escalation procedure should be created to notify management if anything unexpected is reported.
Edge security vendors and products
Multiple classes of security products could be helpful in edge security.
- Firewalls, tunneling and secure communications vendors and products include all the software-defined WAN vendors, because that technology can support secure communications from any edge, including a facility that has local computing. In addition, security and firewall products from major vendors -- Cisco, Juniper, Palo Alto Networks -- can help protect the edge.
- Application control and security at the edge should be a function of IT operations tools, including DevOps -- Chef, Puppet, Ansible -- and container orchestration tools such as Kubernetes. These products are available from a wide variety of sources, including HPE, IBM Red Hat and VMware.
- Threat detection at the edge can be considered either a function of network and systems monitoring, or it can be supported by a specific application set. Popular monitoring tools include Argus, Nagios and Splunk. Specific support for intrusion detection and prevention is available from tools such as SolarWinds Security Event Manager, OSSEC, Snort and Suricata.
- A good problem-tracking and management system is essential for edge computing, particularly if there are many these facilities or they're widely distributed geographically. Popular systems include OSSEC, Tripwire and Wazuh security measures that are applied by the software or hardware that reside there.
All of these tools should be applied within a carefully planned and fully documented edge security practices policy, and the policy should be updated to reflect any change in practices or tools made over time. The document should include a diagram of the edge machine resources, particularly if the edge facility is effectively a mini edge data center. On the diagram, indicate the point at which various security measures are applied and the technology used to provide them.