macrovector - Fotolia
Command tech conversations with IoT terminology you must know
Tech professionals should learn this IoT terminology to put the technology into context, start their journey and join emerging discussions with the same knowledge base.
IoT evolves rapidly with advancements in connectivity, analytics and security. IT admins must understand the industry jargon before they can dig deeper into its nuances and manage an effective deployment.
Organizations adopt IoT technology to simplify tasks, but they won't find deploying IoT simple. Smart thermostats and devices that use apps to turn off lights without the physical flip of a switch are examples of IoT devices. These smart or connected devices represent the basic parts of IoT, but IoT deployments incorporate many other technologies, such as AI, cloud and edge computing, connectivity, and security.
This glossary of 30 IoT terms introduces basic concepts of IoT and works its way to specific considerations that organizations must make to secure and implement IoT.
10 beginner terms to understand IoT in context
Start with the basic IoT terminology to discover important components of IoT and how IoT fits in with other technology trends.
Internet of things. IoT is a system of sensors that collects and exchanges data through a network connection without human involvement. Sensors detect and respond to an input from the physical environment, such as a refrigerator temperature or the vibrations of a machine. IoT devices monitor the state of a machine, environment or person -- the things in the internet of things. IoT derives value from data analysis when admins apply the technology to increase efficiency or better understand processes.
IoT devices. Sometimes referred to as smart or connected devices, these include any device or sensor with computing capabilities that connects to the internet but is not traditionally internet-enabled. For example, a smart thermostat can adjust the temperature of a meeting room based on the number of people present. Smart sensors take input from their surroundings and act with predefined functions when specific conditions are met before the data is sent from the device. Traditional computing devices, such as computers, smartphones or tablets, do not fall under the realm of IoT.
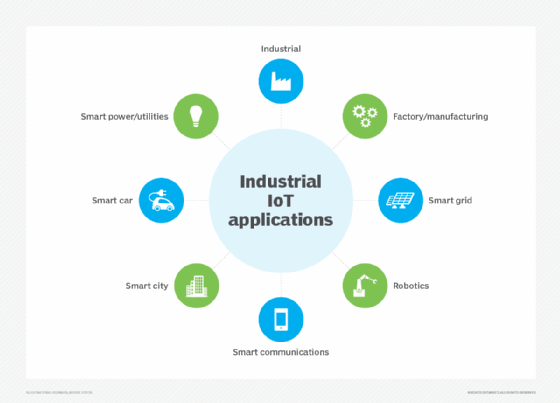
Industrial IoT. IIoT narrows the focus of IoT to the sensors and actuators -- mechanisms that turn energy into motion -- used in a manufacturing or industrial process. IIoT refers to machines that were not previously connected to the internet that now use IoT devices analytics that improve efficiency or business decisions. IIoT use cases include predictive maintenance, supply chain traceability and asset tracking. The architectural components of IoT and IIoT are often similar, but organizations use each for different purposes. IoT covers connected device applications more broadly in many verticals, whereas IIoT devices in manufacturing and utilities deal with critical operational processes.
Fourth industrial revolution. Technologists might hear other professionals refer to IoT as part of the fourth industrial revolution, or Industry 4.0. The idea behind it is that emerging technology trends -- including IoT, virtual reality and AI -- transform the way people live and work, similar to how previous industrial revolutions brought disruptive industrial, technological and digital advancements.
Digital transformation. Some organizations might talk about IoT as the catalyst for digital transformation. This evolution goes beyond just adopting IoT or another emerging technology and requires organizations to rethink and reinvent how they operate at fundamental levels. Organizations must examine and restructure their business strategy and culture to solve problems and optimize processes by turning manual tasks into digital ones.
Big data. IoT data is a subset of big data. IoT devices generate massive amounts of data used for machine learning, predictive modeling and analytics. From the data, organizations identify patterns and trends to inform their business decisions. IoT data requires the infrastructure to better manage, store and analyze a large volume of structured and unstructured data in real time. Organizations use big data, regardless of its source, to give them a competitive advantage to market their products or services, improve their processes and increase customer satisfaction.
IoT analytics. IoT's value comes from what organizations do with the data devices generate. Organizations use analytics to distill actionable information from the plethora of IoT data. IoT analytics tools use sensor data from sources such as manufacturing equipment, smart meters or delivery vehicles for reporting and analysis. IoT analytics challenge organizations with the different data types, the amount of data and the speed required for data processing.
IoT edge computing. Edge computing is the architecture IoT uses to process data close to its generation point, particularly when data processing is time sensitive. IoT edge computing addresses the problem of sending vast amounts of data over the network and processes data on the device itself or at a server close to it. Instead of processing all data for further use, a smart security camera can process and transmit data from the device only when it detects movement, which lessens the load on the network. Any data that does not require real-time analysis can be analyzed in the cloud.
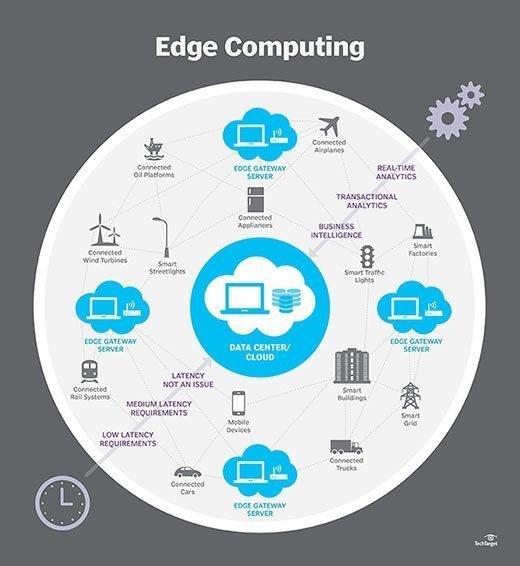
IoT cloud computing. Organizations can use cloud computing services to provide fully managed scalable compute resources for IoT deployments. These services come in the form of infrastructure, platforms or SaaS. Information storage in the cloud gives organizations a backup for disaster recovery and can save them the cost of building the necessary infrastructure in-house.
IoT security. The IoT industry has not prioritized IoT device and network security measures during development, which creates vulnerabilities. Many methods that secure businesses also secure IoT devices, such as firewalls, but connecting devices to the internet presents some unique problems. IoT devices typically exist at the edge of an organization's network and increase the potential attack surface. The small size of IoT devices limits the resources each device can contain, including the space for security measures, such as advanced encryption. IoT standards bodies also lack cohesion, which means organizations have many frameworks to choose from without clear guidelines. Organizations may deploy devices that use different protocols, which complicates security and interoperability. Groups such as the National Institute of Standards and Technology develop industry standards, but these efforts are still in progress.
Dive deeper with intermediate IoT terminology
With a basic understanding of the IoT industry and how IoT fits into organizational strategies, IT administrators can now explore divisions within IoT technology and how IoT works.
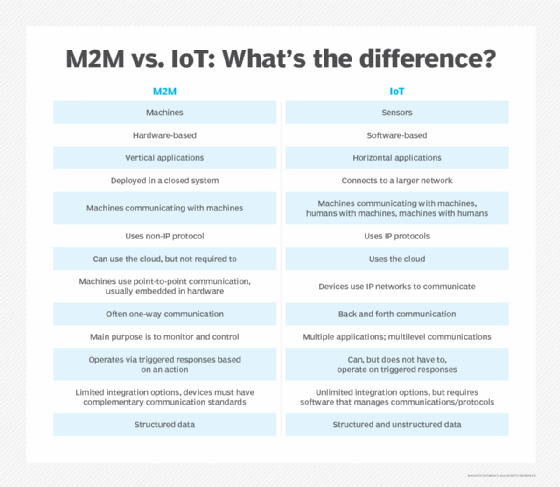
Machine-to-machine. M2M classifies any technology, such as AI, that connected devices use to transfer information or take actions without human interaction. IoT is built on M2M capabilities, but they are not the same. M2M encompasses machines communicating with machines in a closed hardware system. IoT sensors connect to a larger network of machines that communicate with other machines and humans. M2M technology is essential to IoT for use in real time, remote monitoring of patients or equipment, and improving process efficiency. The technology has low-power consumption, the ability to continually or selectively send and receive data, and location-specific triggers for alert devices.
Internet of medical things. IoMT, also known as healthcare IoT, covers medical devices and applications that connect to healthcare networks to analyze data and improve patient care. The most prevalent uses of IoT in healthcare facilities include remote patient monitoring and asset tracking. IoMT comes with increased security risks to patient safety. As the number of connected devices increases, the attack surface gets bigger and hackers have more opportunities to access patient data or devices.
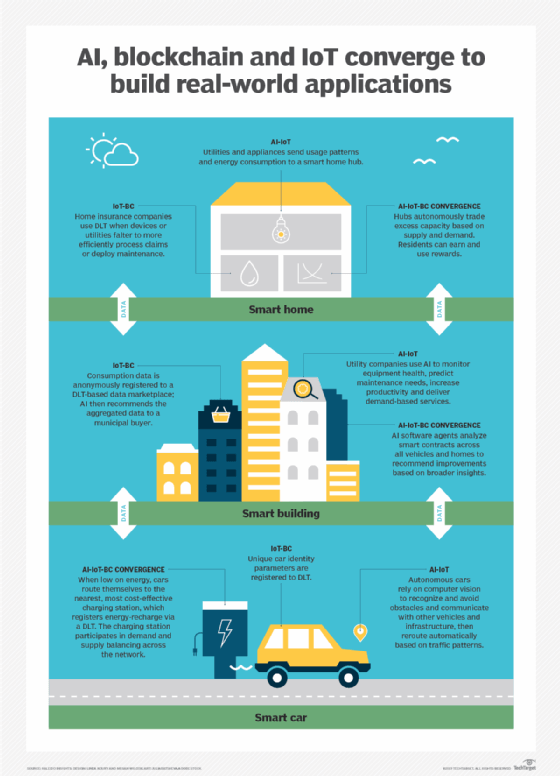
Artificial intelligence of things. AIoT refers to uses where AI combines with IoT to increase operational efficiency and improve data processing for better informed decisions. With AI, IoT devices can make decisions without the need for human intervention. If an IoT device is programmed to monitor the temperature of a machine, AIoT software can register when the temperature goes above or below a desired range and adjust.
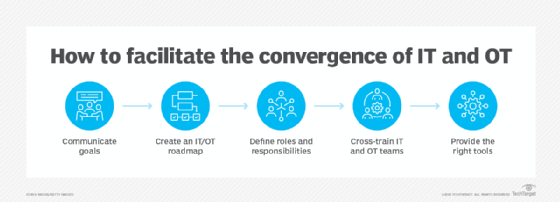
IT/OT convergence. The nature of IoT technology requires IT and operations teams to work together on software, hardware, control systems and networks to succeed. The two teams' convergence can cause conflict in organizations because they often have different priorities and perspectives. IT teams focus on data created by IoT sensors and security. OT teams must incorporate IoT from a practical standpoint and ensure production goes smoothly. Organizations must define the IT and OT roles and responsibilities, outline where IT and OT overlap, and provide the teams with the right tools to support the convergence.
IoT attack surface. IoT adoption expands the attack surface, the total potential vulnerabilities in IoT devices, software and networks, that IT admins must address. Every IoT device connects to a network and has its own IP address, which gives hackers many opportunities to gain access.
IoT platforms. Organizations may use many different types of IoT platforms -- hardware or software that host an application or service -- to manage any aspect of IoT, including devices, data, analytics and security. Platforms simplify the challenges of IoT deployment, management and scalability. Engineers can design their own IoT platforms to manage devices, but many vendors offer IoT platforms as a service, including AWS, Google and Microsoft.
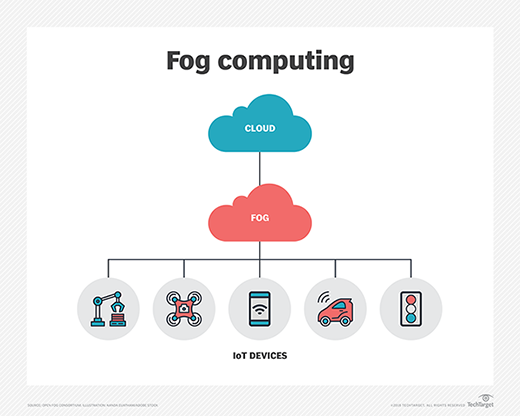
Fog computing. Some IT professionals use the terms fog and edge computing interchangeably, but there are differences between the concepts. Fog computing is the data, compute, storage and applications present between the cloud and the devices that create data. Some organizations use edge computing to strictly mean the compute that happens within network endpoints, absent of any network connections. The data that exists outside of an edge device, but not yet in the cloud, is fog. Fog computing reduces the bandwidth, latency and amount of data sent to the cloud.
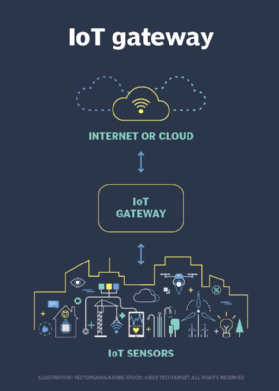
IoT gateway. An IoT gateway device or software program preprocesses all data between IoT devices and the cloud. The gateway aggregates and analyzes the edge data to reduce the volume transferred through the network, which reduces the latency and bandwidth. Without this device, organizations would spend more on data costs in the cloud. Gateways also increase security for data moving to and from the cloud through encryption and tamper detection.
IoT OS. IoT devices require specific technology to transfer data over the internet because of their small size and use in remote locations. IoT developers must design IoT OSes specifically to fit the constraints on size, power and processing capacity. IoT OSes include Ubuntu Core, RIOT, Zephyr, TinyOS and Windows for IoT.
IoT network protocols. Protocols are the rules applied to data format, transmission and receipt for devices to communicate between servers, routers and endpoints, even if the IoT devices use different standards or designs. Examples of IoT protocols include Message Queuing Telemetry Transport (MQTT), Wi-Fi, Bluetooth, Zigbee, LoRaWAN and Z-Wave.
Dig into the details with advanced IoT terminology
Security and data privacy present significant challenges for any organization that uses IoT. IT admins must understand the threats, as well as the different regulations and methods to protect and address data use.
Identity and access management. IAM refers to the policies and technology that IT admins use to manage digital identities and control user access to sensitive information. IAM methods -- such as single sign-on or two-factor authentication -- automate and simplify the processes that assign and track user privileges, and they verify the connection of devices and applications to each other. The growing number of IoT devices that organizations use in remote locations presents a security risk, which IAM can reduce.
Event-driven architecture. EDA makes real-time processing possible through a framework that determines behavior for the production, detection and consumption of events or any significant occurrence in hardware or software. Many IoT uses, such as confirming the legitimacy of a financial transaction or identifying a security threat, require instantaneous processing to respond or react as quickly as possible. Organizations use EDA to produce highly scalable applications and to handle complex event processing from the high volumes of IoT data created.
Real-time analytics. Developers apply real-time analytics to IoT data because they require insights and computer responsiveness almost immediately when the data enters the system. Streaming data architectures with real-time analytics make near-instantaneous decisions through robotic process automation. This analytical type improves efficiency and can prevent damage, injuries or losses, and it can detect network security breaches.
IoT policy. Organizations use an IoT policy document to guide IoT device and deployment developments and address complications throughout the process. Policies differ based on industry, but security and privacy remain top priorities. IoT policies can set the framework for interoperability, standardization and regulatory compliance. Organizations must consider many aspects of their IoT policy, including what access controls IoT devices use, how to prioritize access and how to effectively develop IoT infrastructure.
IoT botnet. Traditional botnets have long plagued the technology landscape with the threat of attackers co-opting hacked devices for illicit ends, such as distributed denial-of-service attacks. The IoT botnet expands the targeted technology to include smart technology such as appliances, internet-connected sensors and automobiles. Attackers can consign any device with an IP address and the ability to transmit data into a botnet. Organizations might have hundreds or tens of thousands of IoT devices, and IT admins must protect each device against cyberthreats.

IoT privacy. IoT privacy refers to the considerations that organizations must make to protect individuals' information that IoT devices collect. As consumers use technology to track and manage more aspects of their lives, they have shown concern for how organizations use the collected data. Most individuals don't know or control how organizations use or monetize the data collected about them. Even though data collected from one sensor might not cause an issue, when it's combined with data from other endpoints and analyzed, organizations could derive sensitive information. Different countries and states have begun to develop legislation around organizations' use of personal data, such as the California Consumer Privacy Act (CCPA) or General Data Protection Regulation (GDPR).
GDPR. This 2018 regulation addresses data privacy laws across the European Union. Under the regulation, organizations must practice greater transparency about how they use personal data and to notify all affected people within 72 hours when an attack breaches their data. Organizations may not process any personally identifiable information unless they meet at least one of six conditions, such as the express consent of the data subject. Although GDPR doesn't focus on IoT, the policies include IoT devices. IoT devices don't often use graphical user interfaces, which makes informing a customer of personal data uses more difficult. Organizations often transfer data processing to the cloud, which can involve numerous parties. GDPR dictates that all parties across a supply chain must be responsible for the data use.

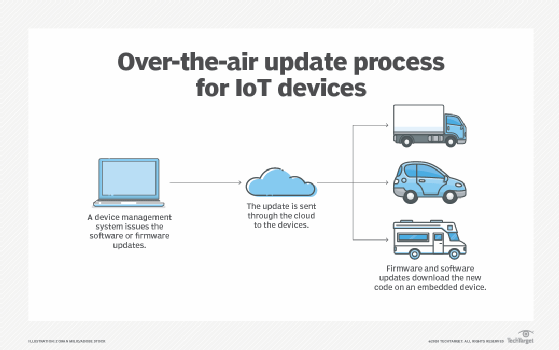
Over-the-air updates. Organizations can patch the software or firmware of IoT devices or deploy new OSes wirelessly with OTA updates. This updating method keeps devices secure and maintains a high level of performance in a scalable way using the same wireless communication paths that devices already send and receive data through. IT admins might need to update difficult-to-reach devices -- such as autonomous vehicles, smart home speakers or utility sensors -- and OTA updates negate the need to patch these devices in person.
Digital twins. Digital twins virtually represent products or workflows across their lifecycles as they evolve. The representation uses a physical item in the world, the digital twin itself in software form and the data that ties the two together. Organizations use the data from the IoT sensors in the physical world to inform the digital twin and to understand its interactions, development and lifecycle management. Developers can test IoT products for performance and reliability to improve real-world performance or predict when a machine will fail. In a production line, a digital twin of the workflow could show where bottlenecks are and how to handle changes in demand effectively.
Blockchain. This distributed ledger creates a permanent, tamperproof record of transactions to build trust in manufacturers. Organizations throughout a supply chain can use IoT sensors to track goods and use blockchain to trace where goods, such as food, came from or to combat counterfeit drugs. Bad actors would have a difficult time faking any information in a blockchain because each computer in the distributed ledger maintains a simultaneously updated and validated copy.