Blockchain for businesses: The ultimate enterprise guide
Despite the scary crypto headlines, enterprise blockchain is becoming more practical. Use our in-depth guide to help manage the risks and plan the best deployment for your needs.
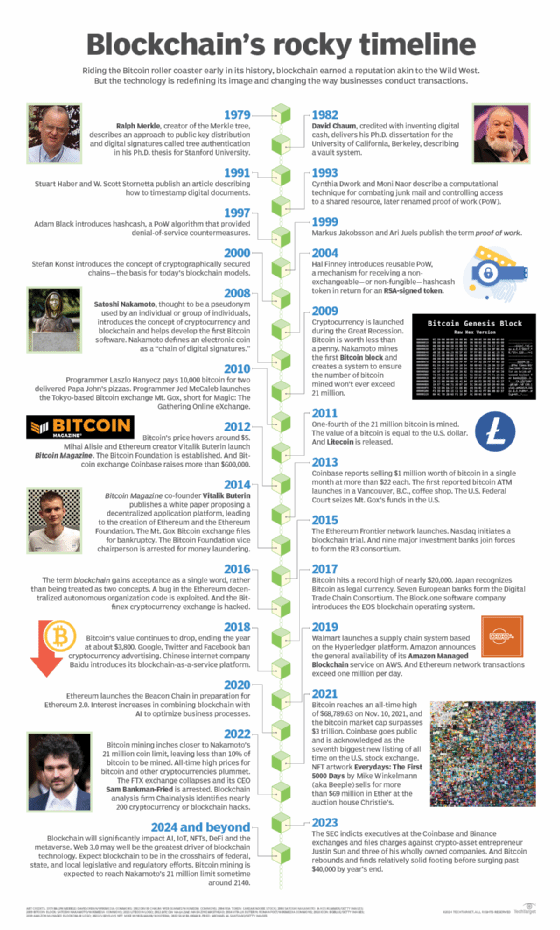
When blockchain hit the scene in 2009 with the release of its first application, the Bitcoin cryptocurrency, it had a Wild West feel akin to the early days of PC hackers. Blockchain used a decentralized, peer-to-peer architecture that let anyone participate, which made it seem too risky for business use.
That started to change in 2016 when a burgeoning open source community began developing complete enterprise platforms, including the Ethereum programmable blockchain and Hyperledger, a framework and tools for building enterprise-grade blockchains.
Household brands like Bumble Bee Foods, IBM, Walmart and Visa touted their blockchain deployments. AT&T, Starbucks and Tesla began accepting cryptocurrency payments, and Bitcoin landed on a few corporate balance sheets. IT heavyweights including Amazon Web Services (AWS), IBM, Oracle and SAP got behind blockchain in a big way.
Then the crypto winter of 2022 brought cryptocurrency prices crashing down. Some crypto exchanges went bankrupt and their CEOs were arrested. The bad news kept coming in 2023, with more arrests and U.S. government regulators throwing the book at the Coinbase and Binance exchanges. Crypto winter turned into the crypto summer of hellfire.
Yet somehow these shocks, not to mention the shuttering of prominent blockchain projects in the insurance, securities and supply chain industries, do not seem to have slowed enterprise blockchain down. Rather than suspending their efforts, companies are moving ahead, but with a greater awareness that risks and expenses must be carefully managed. They've also gotten wise to the blockchain-will-change-the-world hype and homed in on low-risk, quick-payback applications.
"We're finally settling down to realize what we could do with this technology," said Avivah Litan, a Gartner vice president and analyst. "It's almost like we're just getting started after a lot of false hope."
 Avivah Litan
Avivah Litan
Nevertheless, caution is warranted. Blockchain's technical underpinnings and practical implications are hard to grasp. The key is to have a clear picture of what blockchain does and doesn't do; the effects of its various deployment options, especially network architectures; and where it can be used to complement rather than replace existing systems.
This in-depth guide to blockchain for business use has been updated and expanded with new articles, including several on managing the security risks and deploying smart contracts, which have emerged as the main vehicle for business applications. Be sure to click on the links for more detailed explanations and advice.
How does blockchain work?
Blockchain is essentially a database technology with attributes that, taken alone, are not unique to it, but which collectively produce a technological breakthrough in how digital information is stored, verified and exchanged.
Most of blockchain's key attributes come from being a type of distributed ledger technology (DLT). Ledgers have been used for centuries to record financial transactions, more recently in digitized form in ERP and other business software.
In contrast to those centralized approaches, DLTs such as blockchain disseminate copies of the ledger database to the nodes on a network, making each one responsible for recording new transactions and participating in a consensus mechanism to agree on updates to the ledger.
Blockchain's unique data format is another differentiator. Traditional databases store data in rows, columns and files, while blockchain stores it in blocks that are linked together and protected by cryptography.
The data block and transaction-verification mechanisms make it nearly mathematically impossible to hack a blockchain to change data or disrupt transactions. There's no central authority for malicious actors to target, and there's no one player who can take data private, or change the rules without agreement, or whose failure can bring the whole network down. The distributed copies provide data redundancy and transparency.
That's how blockchain achieves what's known as immutability: The ledger is permanent and tamperproof and can therefore be trusted as a faithful record.
Trust is another key attribute of most forms of blockchain. In human interaction, trust means you don't have to take extra steps to check if the information presented is correct, such as asking an authority figure to validate it or only interacting with people you believe to be trustworthy. Similarly, you can trust that the information in a blockchain is accurate -- most of the time, at least. Someone can still input inaccurate information, but you can be sure that whatever was put on the blockchain hasn't been changed.
As with every major computer technology, the picture with blockchain is complicated. Blockchain isn't always uncrackable. Its security and privacy levels, not to mention usefulness, depend heavily on whether the blockchain runs on a public or private network.
Widely available blockchain alternatives provide some of its benefits, such as data security and storage, with less technical risk and cost. For example, FX Everywhere, a system financial services company HSBC uses to exchange foreign currency internally and with Wells Fargo, employs cryptography and consensus on a private distributed ledger that, strictly speaking, isn't a blockchain and doesn't require one.
How can blockchain benefit businesses?
Investing in enterprise blockchain will probably become essential for competitive reasons. Just as corporations paid serious mind to breakthroughs like the PC revolution of the 1970s and 80s and the World Wide Web's mid-90s boom, knowing their competitors were taking advantage of these innovations, many experts believe blockchain will command the same attention.
Herd mentality is not the only thing driving blockchain. The technology has demonstrated its ability to reduce IT costs, expand B2B and B2C networks, enable new products and build wealth.
 Martha Bennett
Martha Bennett
Enterprise blockchain really comes into its own in processes that involve multiple parties, each of which needs access to the same data but has slightly different or out-of-date information, meaning "an enormous amount of time is spent reconciling data," said Martha Bennett, vice president and principal analyst at Forrester Research.
Because blockchain removes middlemen and mostly automates processes that often take time and effort, it has the potential to save IT and labor costs, speed up e-commerce and finance and enable new lines of business. It can also help businesses expand their customer bases, reach them more efficiently and broaden the universe of suppliers and partners. Blockchain benefits primarily derive from the trust blockchain fosters, as well as its built-in privacy, security, data integrity and transparency.
The level of trust in a blockchain makes it possible to do business with unknown parties, potentially expanding markets and the demand for products and services, which in turn can boost profits.
Being able to also trust the accuracy of the data, as well as believe that the system itself is essentially impermeable and that, in most cases, privacy is assured, can reduce fraud, eliminate data leaks and help bring in more customers and partners. It can also cut data management costs, boost data quality and facilitate auditing.
The transparency of blockchains has benefits in supply chain management, visibility and traceability. Blockchain is already making it feasible to extend supply chain transparency to the smallest suppliers, such as coffee and lettuce growers and tuna fishing operations, while shoring up trust in information about product provenance as the goods move through the supply chain to consumers.
Other blockchain benefits to enterprises include the following:
- Tokenization. Tokenizing assets makes a greater variety of assets, from digital art to carbon credits to industrial machinery, tradeable online.
- Innovation. Blockchain's special qualities can be applied to old problems, such as verifying academic credentials.
- Decentralization. Decentralized management is helpful when businesses must interact as peers but no one wants responsibility for maintaining the system, as in supply chains and research communities.
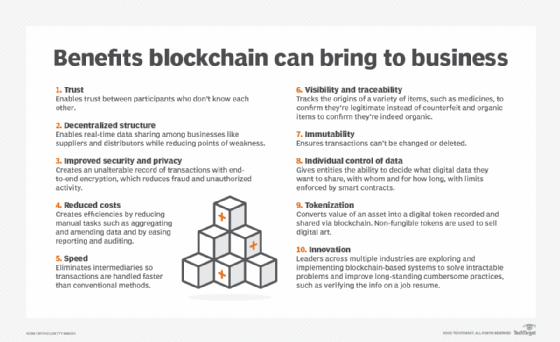
That exact set of innovations isn't available with any other technology, according to Litan. "You can't get a shared system of record based on immutable data or the ability to tokenize assets right within the protocol," she said. "The ability to tokenize assets and track them through their lifecycle on an immutable chain has tremendous value."
While exorbitantly priced and ridiculous-sounding non-fungible tokens (NFTs) make the evening news, enterprise blockchain developers see more important opportunities in expanding tokenization to create new forms of identity verification and digital commerce. "There are probably a lot more tokens in blockchain applications today than many people realize," Bennett said. "In many of the track-and-trace applications that are live today, some of those already represent the asset that's being tracked as a token."
What are blockchain applications for businesses?
The most important application of blockchain for business could be smart contracts, which play a dual role as foundational components of blockchain infrastructure and software development and as an application of the technology.
A smart contract is most easily understood as a program that uses business logic to execute agreements and transactions between blockchain participants.
Smart contracts have many uses in business. They can completely automate the exchange of money, delivery of services, granting of access to digital content and enforcement of privacy protections.
For example, a blockchain freight-invoicing application deployed by Walmart Canada uses smart contracts to pull live shipment data into invoices and send preapproved payments once the terms of the shipping agreement are met. Bennett called it a "poster child" for how a well-designed blockchain application can save significant time and money by minimizing data reconciliation processes and disputes.
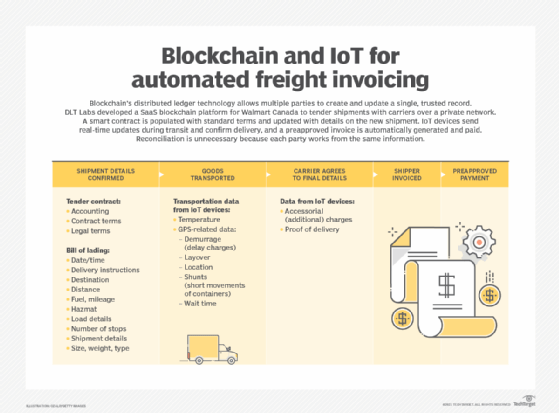
Here are other blockchain applications with business uses:
- Cybersecurity. Blockchain's strong encryption and other security safeguards make it another tool in the security toolbox.
- Cryptocurrency. Bitcoin and other digital currencies have moved past the fad stage as high-profile companies like Tesla add it to their investment portfolios and accept it as payment for some products.
- IoT. Blockchain is ensuring the integrity of data collected from sensors as it moves up the supply chain from fields and factory floors in applications for asset management, environmental compliance and traceability. It could also free up machine-to-machine communication so semi-autonomous machines can order their own replacement parts and pay for maintenance.
- Storage. Blockchain's decentralized, peer-to-peer architecture makes it possible to piece together the unused disk space of blockchain participants, creating blockchain storage.
Blockchain use cases in real-world industries
Blockchain use cases tend to cluster in industries that are deep-pocketed and have tech-savvy market leaders who can make the business case for and then implement blockchain business applications, which typically require substantial coordination and transactions among numerous partners -- or even competitors.
Examples of sectors that are finding uses for blockchain include the following:
Supply chain. Blockchain expands the number of suppliers and buyers and helps ensure the integrity of data passing through the supply chain, thereby getting closer to the elusive goals of supply chain visibility and transparency. One example is IBM Food Trust, a blockchain network that Walmart has used since 2018 to track leafy greens.
Banking and finance. Blockchain use cases in finance fall into two distinct segments: cryptocurrency and decentralized finance, or DeFi. Despite the recent setbacks, cryptocurrency continues to gain credibility as an alternative payment mechanism in a world monetary system that is largely run by government central banks and big payment providers such as Mastercard and Visa.
At the same time, DeFi is emerging as a potential replacement for other processes traditionally handled by banks and financial service providers -- namely credit, insurance, banking and investments. By using smart contracts, individuals might be able to lend each other money, pay interest, insure against loss and trade asset derivatives.
Optimistic observers predict these applications will bring about a "blockchain economy" in which cryptocurrency has largely replaced today's monetary systems and people and machines manage business processes and exchange value without intermediaries.
Meanwhile, financial services companies are augmenting their traditional centralized finance architectures with decentralized finance technology. They're also using blockchain to process payments more efficiently on private networks instead of having to go through traditional clearinghouses, which can take a day or more.
Healthcare. Blockchain security, privacy, data integrity and anonymity are enabling new uses of the genomic data and medical records of individuals to support pharmaceutical research and make it easier to transmit electronic medical records.
Government. Blockchain could make it easier -- and legal -- to transmit personal identification electronically, vote online, acquire a passport and prepare legal documents and regulatory filings, such as mortgage deeds and financial reports.
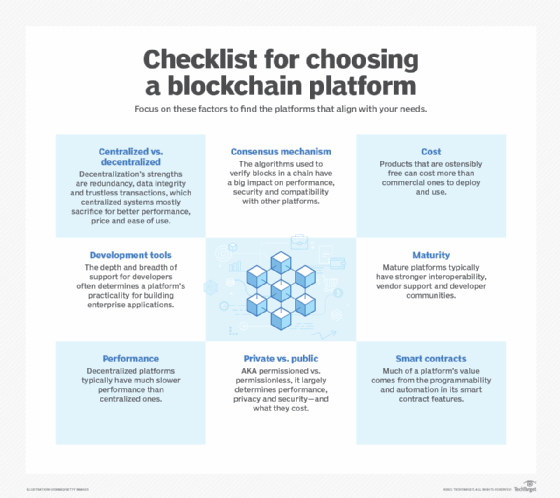
What are the different types of blockchain technology?
The different types of blockchain are categorized by how open or closed they are to letting participants do the main work of the blockchain, which includes transacting business on it and verifying the accuracy of each block that gets added to the blockchain.
Here are the major types:
- Public (permissionless) blockchain. A public blockchain doesn't require permission to join and is transparent to all participants. It's the kind of blockchain where cryptocurrency lives. It's also the slowest because opening the blockchain's consensus process to so many participants makes data verification more tedious -- but also less vulnerable to hacking or control by a dominant actor, according to blockchain advocates.
- Private (permissioned) blockchain. Running on a closed network, often under the control of a single entity, this type of blockchain usually has the same decentralization and peer-to-peer architecture as public blockchain but on a much smaller scale, which boosts performance. Ironically, trust is weaker than on a public blockchain because the owner or central node decides what's valid. Security can also be weaker because it's easier for a small number of nodes to dominate the consensus mechanism used to validate transactions. Most high-profile blockchain deployments are on private blockchains.
- Hybrid blockchain. Unsurprisingly, a hybrid blockchain combines aspects of public and private blockchains. Organizations can use it to segment some data and transactions behind a permission scheme while maintaining connections to the public side. The blockchain security risks and data integrity issues of private blockchain are mitigated by not allowing the owner to alter transactions, and performance tends to be better than a public blockchain's. Users joining a hybrid blockchain have privacy until they enter into a transaction.
- Consortium blockchain. This is a lot like private blockchain, but it's controlled by a group instead of a single entity. There's less security vulnerability than is typical with private blockchain, though one node is responsible for validating transactions. Evidence is emerging that consortium blockchains are too expensive and don't provide a clear ROI for participants, according to Litan. Some have gone out of business, including the insurance consortium B3i and TradeLens, a supply chain network started by IBM and global shipping company Maersk.
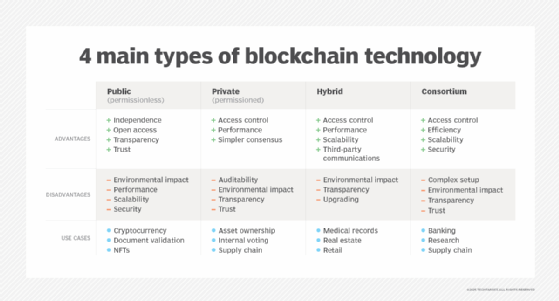
Enterprise blockchain experts disagree on the permissioned vs. permissionless choice. It's undeniable that most of the successful deployments so far have been on private blockchains, presumably because corporations want control over who can participate, and even the most prominent public platforms also cater to private blockchain development.
But Paul Brody, global blockchain leader at consulting firm EY, says public blockchains are best because they encourage the high participation rate that will make blockchain networks valuable. He wrote an article for this guide on how to implement blockchain.
What are the risks and challenges of blockchain adoption?
Blockchain represents a fundamental architectural change for data centers, which usually employ centralized databases and concentrate their computing power in fewer locations than the typical blockchain. Meeting the anticipated demand for blockchain will require major infrastructure upgrades. On the other hand, blockchain's data integrity, storage and security advantages could improve data center reliability.
Adopting blockchain for serious enterprise use carries above-average risks of choosing the wrong platform, incurring project cost overruns and delays, and failing to achieve positive ROI.
Smart contract security, in particular, is problematical. Smart contracts can move large amounts of valuable data and financial resources, which makes them attractive targets.
A smart contract might be programmed with faulty logic or interact with off-chain financial systems in ways that hackers can infiltrate. Transactions can fail to complete and leave openings to exploit the system. Many weaknesses come from malicious actors figuring out ways to exploit the rules of the blockchain, not from any breakdown of the rules themselves or prohibited accessing of a network.
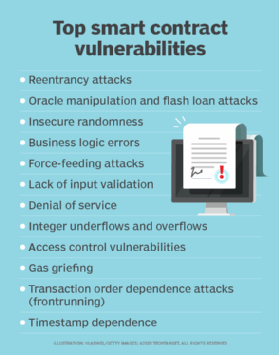
Smart contract bugs generally can't be patched once a contract is deployed because code and data already on the blockchain are unchangeable by design. That means smart contract developers are under pressure to get things right the first time. Smart contact best practices, such as using the simplest possible design, limiting unnecessary user access and testing exhaustively can help minimize vulnerabilities.
Another way to address the cybersecurity threat before deployment is to conduct a smart contract audit, which is designed to spot coding and logic errors as well as performance and reliability issues using both automated and manual procedures. Organizations that don't have the required expertise can hire outside auditing firms.
Other common blockchain challenges include the following:
- Lack of adoption. Blockchain -- especially public blockchain -- requires large numbers of participants for most of its benefits to be realized. Until more companies are willing to take the leap and try out blockchain, those that do are likely to find a small universe of trading partners waiting for them, according to market researchers.
- Skills gap. Blockchain know-how is in short supply, though that's rapidly changing as training and certification rises along with the demand -- and pay -- for blockchain developers and engineers.
- Lack of trust. Blockchain is still so new that many businesses won't have confidence in its unfamiliar security and data-integrity mechanisms. In response, they'll want to control the system in a private blockchain but will lose some transparency and data redundancy in the process.
- Scalability. The redundancy and distributed nature of blockchain's computing resources generally add cost and hurt performance. Those drawbacks are a big reason most early enterprise blockchains are private for a select group of participants. The proof-of-work (PoW) consensus mechanism used by many blockchains requires enormous volumes of calculations. Ethereum and other organizations have started to address the problem by moving to proof of stake, a mechanism said to be more efficient.
- Environmental sustainability. There is a growing awareness that blockchain's compute-intensive processes, especially PoW consensus and bitcoin mining, are among the biggest users of natural resources in all of IT. Governments are considering regulating the industry, and blockchain vendors have begun taking steps to reduce their carbon footprints.
Blockchain implementation best practices
Achieving positive ROI from what are likely to be expensive blockchain projects requires an acute sense of blockchain's unique benefits and focusing only on problems it's best suited to solve.
 Paul Brody
Paul Brody
That usually entails taking full advantage of smart contracts and tokenization, according to EY's Brody, which in turn means fully appreciating the automation and programmability available in smart contracts, and not confusing their use with moving documents back and forth. Tokens are the means for moving value rather than information, which is essential to realizing blockchain's potential, Brody stressed.
He also advised not obsessing over finding the best technology and instead going for the network with the most users.
Finally, don't use blockchain to fix a problem already solved with another technology. It's a waste of resources and adds risk.
Blockchain deployment options
Deploying blockchain is a heavy lift for most companies. It requires substantial upfront design work, technology selection, software development and testing. Companies typically run pilots, only a fraction of which go into production. They often turn to system integrators, such as Accenture, Deloitte, EY, KPMG and PwC, to manage their blockchain projects from start to finish.
Blockchain-as-a-service providers offer a shortcut by bundling the smart contract technology, blockchains and network infrastructure. BaaS has emerged as a popular choice because it removes much of the legwork of setting up a blockchain. Prominent BaaS players include AWS, IBM, Oracle, SAP and VMware.
Litan said the current generation of BaaS platforms has brought the cost of blockchain down enormously and saved customers millions of dollars in consulting fees. Some specialize in the data-exchange needs of specific industries, such as healthcare and automotive. Companies are increasingly turning to BaaS to integrate their suppliers and customers rather than going through the organizational challenges of setting up a consortium. Automaker BMW is using BaaS to improve its repair ecosystem, she said.
BaaS features vary widely. Some have application templates, off-the-shelf applications and support for multiple cloud platforms and interoperability. "What they all have in common is their lower costs. They get you up and running," Litan said.
Data needn't be decentralized for the BaaS to provide blockchain's main benefits: tokenization, smart contracts and immutability. If the participants are having a hard time deciding who should be in control, a distributed ledger might be preferable, but, otherwise, a centralized approach is best.
"These [BaaS] vendors have all said their clients don't really care about decentralization, they just care about tokenizing the assets, the immutability and the smart contracts," Litan said. Companies that need the fault tolerance of a decentralized blockchain can add a public sidechain.
Some organizations will still want to develop most of the infrastructure and applications in-house. For that, they'll likely turn to one of the open source platforms for deploying blockchains and smart contracts and the many development tools that support them.
Blockchain tools and vendor market
The number and quality of blockchain platforms with enterprise-class blockchain development tools and architectures have reached a point where most companies can find a suitable platform and supportive community of developers and system integrators.
 Suseel Menon
Suseel Menon
Here are the top three platforms for enterprise blockchain, according to Suseel Menon, a senior analyst at Everest Group.
Ethereum. This open source community offers one of the oldest blockchain platforms and the one with the most support from developers and IT vendors, with companies like Cisco, Intel, J.P. Morgan, Mastercard, Microsoft, Samsung, Toyota and Visa participating in its member alliance. It bills itself as a programmable blockchain -- an apt description. Ethereum provides the underlying network and the blockchain itself, comparable to the one that Bitcoin is on. Ethereum's competing cryptocurrency -- Ether, or ETH for short -- plays an additional role as the exchange medium and token for all operations on the network, but the platform's greatest relevance to enterprises is its wealth of tools for developing smart contracts and blockchain decentralized applications (dApps). Ethereum also provides a marketplace for applications, including games, financial services and exchanges for NFTs, an increasingly popular type of digital asset on blockchains.
Hyperledger. This open source community is backed by the Linux Foundation, the consortium behind the popular Linux operating system, as well as by Intel, SAP Ariba and IBM, the latter of which uses Hyperledger as the basis for its BaaS offering. The platform has a strong focus on private blockchains for enterprises, with extra features for enforcing privacy, and provides frameworks, development tools and software libraries of components that companies can plug in to build applications. Hyperledger's name underscores its emphasis on distributed ledgers. Hyperledger Fabric is the modular DLT platform behind many blockchain projects. Another popular tool, especially for supply chain use, is Hyperledger Sawtooth, which abstracts the application layer from the underlying core architecture so companies can focus on writing the business rules for smart contracts. Sawtooth also has alternative consensus algorithms that can improve blockchain performance.
Corda. From the R3 consortium, Corda is billed as a private, permissioned blockchain for DLT applications, though others debate whether it's a true blockchain because it doesn't batch transactions in blocks. R3 claims its way of linking transactions performs better than the traditional method. Corda is popular in financial services. It counts Bank of America and HSBC as proponents and is getting strong interest from insurers.
Other major blockchain platforms, including the IBM Blockchain Platform, Solana and Tezos, have strong smart contract features. Another option is a smart contract platform. Some specialize in private blockchains or providing tools for programming smart contracts that can be deployed on different blockchains.
Blockchain jobs, roles and responsibilities
Blockchain is still very much an emerging technology, and the skills needed to develop and use it are in short supply.
Blockchain developer and blockchain engineer are two common job titles, analogous to the development and engineering roles that have long defined general software and web development, but with blockchain-specific skills added, such as experience using the major open source platforms, especially Ethereum and Hyperledger. For example, a blockchain developer might need to know how to develop a smart contract to run on Ethereum.
Some blockchain developers specialize in dApps and smart contracts, while others focus on the plumbing, such as cryptography and consensus algorithms. Most also need to have web development and cloud infrastructure skills, such as Java and Kubernetes experience.
The online job board Cryptocurrency Jobs, which also serves the enterprise blockchain market, recently listed 180 developer and engineer jobs out of 615 postings.
Additionally, user experience designers work on the look and feel of dApps, and web developers program web applications that incorporate blockchain. Data scientists and financial analysts are also hired for blockchain projects.
Training for these jobs is available online and in secondary education, as are certification programs.
Notable blockchain successes and failures
The 2022 crash in cryptocurrency valuations and trading volumes, followed by the collapse of the FTX exchange and the arrest of its CEO, Sam Bankman-Fried, amplified fears about cryptocurrency's riskiness.
The market has mostly recovered, but more bad news, including the U.S. Securities and Exchange Commission's indictment of executives at the Coinbase and Binance cryptocurrency exchanges, continues to cast a pall over both cryptocurrency and blockchain. The expectation of new government regulation of cryptocurrency adds to the uncertainty, though some observers say establishing rules of the road will confer legitimacy, build trust and attract more investment.
There have been other notable blockchain failures.
In November 2022, the Australian Stock Exchange scrapped a seven-year plan to move its trading platform to blockchain, took a $168 million charge and said it would restart with different technology.
The blockchain attacks put the lie to blockchain's supposed invulnerability. Blockchain data provider Chainalysis identified nearly 200 cryptocurrency or blockchain hacks that resulted in $3.8 billion in losses in 2022, the worst year ever. In the biggest incident, $625 million worth of Ether and USDC stablecoin were stolen from the Ronin Network, a video game blockchain. The U.S. Treasury Department determined that a North Korean hacker collective was behind the attack.
Criminals have found other clever ways to use cryptocurrency to separate people from their money. Common cryptocurrency scams include fake cryptocurrency exchanges, bitcoin investment schemes where scammers request exorbitant fees or personal information in exchange for a promise of huge profits, and rug pulls where thieves abscond with funds invested in projects, cryptocurrencies or NFTs that turn out to be worthless.
In addition, several impressive early deployments were shut down in the past year. Perhaps the biggest closure came in November 2022 when Maersk killed the TradeLens blockchain it co-developed with IBM because not enough shippers signed up. In a blog post, Litan wrote that the lesson is large consortiums that try to meet the unique needs of every participant are too complex and expensive to ever be profitable.
Despite all this, cryptocurrency has gone mainstream and entered the daily discourse in the business media. Gartner said the global cryptocurrency market reached $2 trillion in 2022. McKinsey predicted that by 2027, 10% of global gross domestic product could be from blockchain transactions.
However, most market estimates of non-crypto enterprise applications of blockchain are a tiny fraction of the cryptocurrency market -- in the $5-10 billion range -- though both markets are expected to continue their rapid growth.
While cryptocurrency fraud, bankruptcies and blockchain hacks have cast doubt on blockchain's feasibility for enterprise use, the technology continues to advance. IT vendors keep investing in it and convincing customers that it deserves a meaningful role in their business and IT planning.
For more on blockchain security
This collection leads you through blockchain's vulnerabilities, gives tips on how to address them and explains how blockchain can augment cybersecurity.
Banking giant J.P. Morgan maintains a blockchain infrastructure unit, and since 2017 it has run a private payment network called Liink. In 2022, it connected Liink to Visa's private blockchain to streamline cross-border payments.
Litan noted a strong trend toward tokenization of digital assets, citing the Franklin Templeton and Goldman Sachs financial services firms. Among nonfinancial uses, she said the blockchain projects with staying power involve environmental, social and governance compliance.
For example, Williams, a large supplier of natural gas in the U.S., is using IoT sensors and a blockchain with a centralized ledger to tokenize its production process and provide purchasers with certificates of the fuel's contents.
Gas pipeline operators in other countries are interested. "It just turns out that the ledger is a good place to keep this data," Litan said. "You can trade it, too, because you have a trustworthy source showing the credit and the debit."
What is the future of blockchain?
Blockchain is one of a handful of cloud-based technologies considered to be essential in digital transformation and the "intelligent" enterprise, along with AI, advanced analytics and IoT.
Among the most promising blockchain trends is the merging of AI with blockchain. AI needs copious amounts of data to apply its machine learning algorithms to recognize patterns, predict future outcomes and "learn" how to take over tasks done by humans. Blockchain could potentially unleash a torrent of new data, in part by providing the privacy and security users need to feel confident about sharing more of their personal information. AI, in turn, could improve the efficiency of blockchain's cumbersome consensus and verification process.
The broader context in which blockchain is evolving has changed significantly. Blockchain is now understood to be foundational to the next generation of the internet, Web 3.0. Blockchain and popular applications like NFTs and cryptocurrency are also essential elements of the metaverse, the emerging virtual, 3D world that will run on Web 3.0.
Blockchain could explode in popularity, especially if the entire Web 3.0 vision becomes a reality. Major vendors are beginning to implement parts of Web 3.0, and the hype surrounding it alone could drive demand for blockchain. Products and services built on blockchain are increasingly pitched as Web 3.0 vehicles.
A lot still has to happen before blockchain can replace today's methods of sharing data and conducting transactions over digital networks. Now that blockchain development tools and frameworks are proving their viability for enterprise applications, that day seems more like a real possibility than a distant mirage.








